- Wahoo's largest bike computer is the fitness accessory I didn't know I needed
- Thanks to AI, the data reckoning has arrived
- Has Oracle knocked SAP off the ERP throne?
- YouTube celebrates 20 years with new features, cool tricks, and some truly mind-blowing stats
- Here's how you can try Audible for $1 per month
Organized Cybercrime Cases: What CISOs Need to Know

Risk Management
Jon Clay, VP of Threat Intelligence at Trend Micro, explores the latest Trend Micro Research covering Access as a Service (AaaS), an emerging business model selling all-access passes to other malicious actors.
Read time: ( words)
What is access as a service?
Recently, Trend Micro Research analyzed a new service offering, called Access as a Service (AaaS), in the undergrounds whereby malicious actors are selling access into business networks. The service is part of the overall cybercrime as a service (CaaS) that comprises many different offerings such as ransomware as a service (RaaS).
AaaS is composed of individuals and groups that use numerous methods to obtain remote access into an organization’s network. There are three types of AaaS sellers:
- Opportunistic actors who noticed a demand and decided to turn a profit.
- Dedicated sellers—their full-time job is gaining and selling access. They even market their services and leverage their extensive network to make sales.
- Online shops, which typically only guarantee access to a single machine, not a network or corporation.
Groups who specialize in gaining access to networks and then purposely selling it to others are more worrisome as their access is usually solid and ensures their buyers that they can deliver their service. Both AaaS actors can be troublesome, but the latter is certainly the group that will trouble more organizations due to the complexity of attributing the initial attacker.
AaaS targets
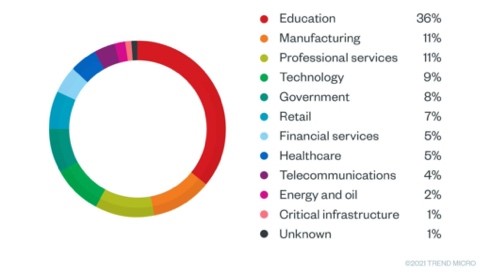
As with all types of cyberattacks, certain industries are more targeted than others. Trend Micro Research analyzed over 900 access broker listings and determined 36% offered access to colleges, universities, and K-12 schools. This is unsurprising considering the uptick of data breaches in the education sector, and the fact schools possess a goldmine of personal information that can be sold in underground markets or ransomed.
Cybercrime trends
AaaS is part of a developing trend in cybercrime, which is the increased specialization of services within CaaS and increased collaboration among these groups. We’re now seeing people and groups specialize in various parts of the attack lifecycle. This means that we’re likely going to see less mistakes made leading to detections, and we should expect multiple groups colonizing an infected network. Thinking from an incident response mentality, this means they will have to identify these different groups completing specific aspects of the overall attack, making it tougher to detect and stop attacks.
AaaS defense strategies
As mentioned earlier, attacks where access was gained and handed off to another group can be trickier to stop due to the change in attacker behavior. Therefore, it’s crucial for CISOs and security teams to implement a cybersecurity defense strategy that focuses on detecting and preventing the initial access breach. The earlier you can detect the initial access of an attack, the more likely you can prevent the following components of the attack lifecycle from occurring, like ransomware. Here are other components to consider when creating an effective security strategy:
- Monitor public breaches and the criminal underground for any offerings of access to your network. If you see or suspect your network’s access is being peddled, trigger a password reset to prevent credential dumping.
- Set up two-factor authentication (2FA) to prevent malicious actors gaining access via leaked credentials.
- Make sure incident response (IR) teams understand the multi-attacker scenario and know where to focus their efforts.
- Apply a Zero Trust approach by using a platform with XDR capabilities to continually verify and monitor users to ensure only those who should be accessing your network are doing so. A platform helps consolidate all correlated user activity and data for more visibility.
- Leverage trusted frameworks such as the National Institute of Standards and Technology (NIST) and the European Union Agency for Cybersecurity (ENISA). You can view their collection of updated password guidelines here.
For more insights into AaaS and how to strengthen your defense strategy, check out Investigating the Emerging Access-as-a-Service Market or explore our Deep Web research for additional information on the underground cybercrime markets.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

